What is CUI (Controlled Unclassified Information)? A Comprehensive Guide
Controlled Unclassified Information (CUI) refers to information that requires safeguarding or dissemination controls, consistent with applicable laws, regulations, and government-wide policies, but is not classified under Executive Order 13526 or the Atomic Energy Act. CUI is a critical concept within the realm of information security, particularly in the context of government and defense operations. This article will provide a detailed overview of CUI, its significance, types, handling procedures, and more.
Understanding Controlled Unclassified Information (CUI)
Controlled Unclassified Information is designed to protect sensitive information that, while not classified, still requires a level of protection due to its potential impact on national security, privacy, or other critical interests. The CUI program was established to standardize the way the federal government handles unclassified information that needs protection.
Key Objectives of CUI
- Standardization: Establish a uniform approach to managing unclassified information across federal agencies.
- Protection: Ensure that sensitive information is adequately protected from unauthorized access and disclosure.
- Compliance: Align with various laws and regulations that mandate the protection of certain types of information.
Types of CUI
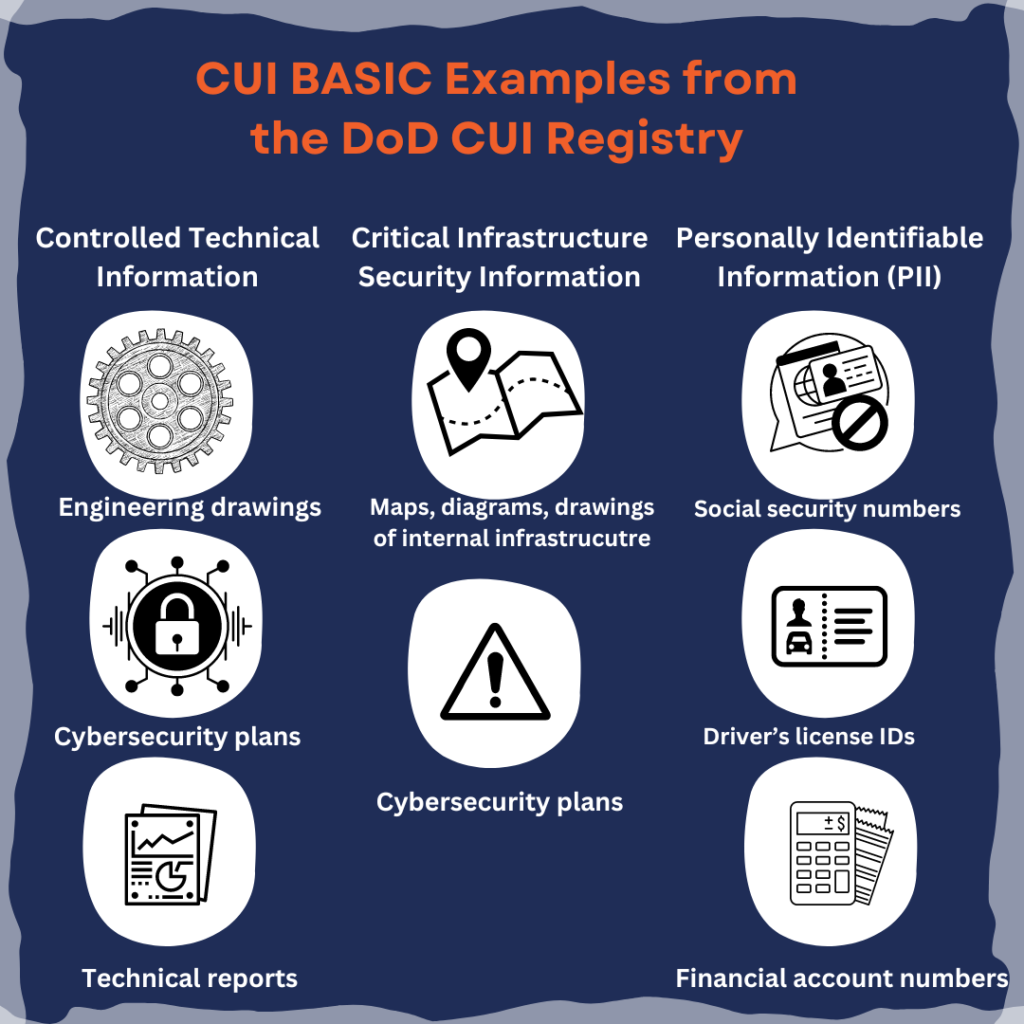
CUI is categorized into several types, each with specific handling and protection requirements. Some common categories include:
- Privacy Information: Personal data that must be protected to maintain individual privacy, such as Social Security numbers and medical records.
- Financial Information: Sensitive financial data, including bank account numbers, credit card information, and financial statements.
- Proprietary Information: Information that is owned by a company or individual and is not intended for public disclosure, such as trade secrets and business plans.
- Law Enforcement Information: Information related to law enforcement activities that must be protected to ensure operational integrity and privacy.
- Critical Infrastructure Information: Data related to the security and resilience of critical infrastructure sectors, such as energy, transportation, and communications.
CUI Program Implementation
The implementation of the CUI program is guided by the National Archives and Records Administration (NARA) and the CUI Executive Order (EO) 13556. Here are the key steps involved in implementing a CUI program:
- Identification: Determine which information qualifies as CUI based on established criteria.
- Marking: Clearly mark documents and electronic files containing CUI to indicate their status and handling requirements.
- Access Control: Limit access to CUI to authorized personnel only, ensuring that individuals who do not have a need to know cannot access this information.
- Training: Provide training to employees on the proper handling and protection of CUI to ensure compliance with established policies.
- Incident Reporting: Establish procedures for reporting any incidents involving unauthorized access, disclosure, or loss of CUI.
Handling and Protecting CUI
Proper handling and protection of CUI are crucial to maintaining its confidentiality and integrity. Here are some best practices for managing CUI:
- Secure Storage: Store physical documents containing CUI in locked cabinets or secure areas. For electronic files, use encrypted storage solutions.
- Controlled Access: Implement access controls to ensure that only authorized personnel can access CUI. This may include using passwords, biometric authentication, or security badges.
- Data Transmission: When transmitting CUI, use secure methods such as encrypted email or secure file transfer protocols to protect the information from interception.
- Disposal Procedures: Establish procedures for the secure disposal of CUI, including shredding physical documents and securely deleting electronic files.
Frequently Asked Questions (FAQ)
1. What is the purpose of CUI?
The purpose of CUI is to protect sensitive information that requires safeguarding but is not classified. It aims to standardize the handling of unclassified information across federal agencies.
2. Who is responsible for managing CUI?
Every federal agency is responsible for managing CUI within its operations. This includes identifying, marking, and protecting CUI in accordance with established policies.
3. How is CUI marked?
CUI is marked with specific designations that indicate its status and handling requirements. This may include the CUI logo and a designation that specifies the category of the information.
4. Can CUI be shared with non-government entities?
Yes, CUI can be shared with non-government entities, but only under specific conditions and with appropriate safeguards in place to protect the information.
5. What happens if CUI is improperly handled or disclosed?
Improper handling or disclosure of CUI can result in disciplinary actions, legal consequences, and damage to national security or individual privacy.
Table with Wikipedia or .gov Link
| Metric | Value |
|---|---|
| Established by | Executive Order 13556 |
| Governing body | National Archives and Records Administration (NARA) |
| Types of CUI | Privacy Information, Financial Information, Proprietary Information, Law Enforcement Information, Critical Infrastructure Information |
| Required training | Yes, for personnel handling CUI |
| Reporting incidents | Mandatory for unauthorized access or disclosure |
For more information on Controlled Unclassified Information, visit the National Archives and Records Administration (NARA) page on CUI.
Conclusion
Controlled Unclassified Information (CUI) plays a vital role in safeguarding sensitive information that, while not classified, still requires protection. Understanding the types, handling procedures, and compliance requirements associated with CUI is essential for federal agencies and their employees. By implementing proper CUI management practices, organizations can ensure the confidentiality and integrity of sensitive information, thereby contributing to national security and the protection of individual privacy.